Managing access and permissions in AWS is critical to maintaining the security and integrity of your cloud environment. IAM is a powerful framework designed by AWS, and it’s your responsibility to make the most of it and keep your projects safe from hackers.
1. Create an IAM group to isolate access
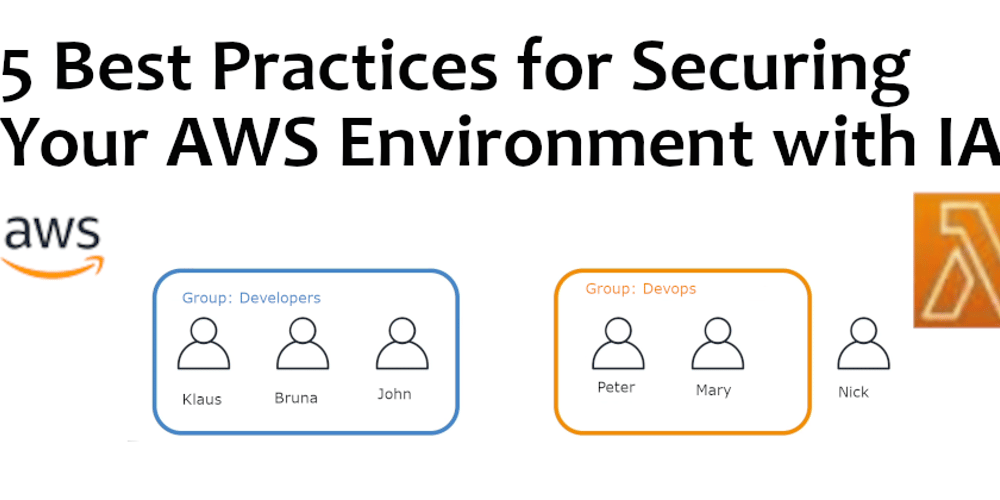
An IAM group is a collection of IAM users. Instead of assigning the policy directly to each user, you can attach a policy to a group. Users in a group inherit the group’s permissions, making it easier to manage access at scale.
In this diagram, you have the flexibility to assign custom permissions specifically to Nick. Additionally, you can grant additional custom permissions to any other user in any group as needed.
2. Principle of least privilege
Grant users, roles, and services only the permissions they need to perform their tasks. Avoid using policies that are too permissive, such as administrator access or * permissions.
Instead of this policy:
{
"Effect": "Allow",
"Action": "*",
"Resource": "*"
}
Use short permissions for specific operations and resources:
{
"Effect": "Allow",
"Action": ["s3:GetObject"],
"Resource": ["arn:aws:s3:::example-bucket/*"]
}
3. Use multi-factor authentication (MFA)
Enable MFA for all users, especially for high-privilege accounts such as root or administrator users with AdministratorAccess policy. MFA provides an extra layer of security by requiring a second factor, either using your mobile device or an external device.
There are some apps you can download on the app store like Google Authenticator (my top choice), authy.
4. Avoid using the root account for daily operations
The root account has unrestricted access to all resources in your AWS environment. Use it only for initial account setup and specific administrative tasks. Create separate IAM users or roles for daily operations.
5. Set password policies for your users
Access keys and passwords should be rotated regularly to reduce the risk of unauthorized access.
You can set this in:
IAM > Account Settings > Edit Password Policy
Comply with industry standards or company policy.
My thoughts on this:
AWS is responsible for everything they do, such as their infrastructure, network security, and vulnerability analysis of the services they provide.
But with IAM, you are responsible for creating your own users, groups, roles, policies, monitoring, enabling MFA for accounts, rotating keys frequently, analyzing access patterns, and reviewing permissions granted to groups/users/roles.
Never forget these concepts as it can lead to security breaches in your organization and I hope I can help you in some way!