Booking.com Phishers May Leave You With Reservations – Krebs on Security
Many cybercrime innovations make it easier for scammers to profit from your upcoming travel plans. This story explores a recent spear phishing campaign that occurred when a phishing incident occurred at a hotel in California. Booking.com Credentials stolen. We’ll also explore a range of cybercriminal services targeting phishers who target hotels relying on the world’s most visited travel website.
According to market share website statista.comBooking.com is by far the busiest travel service on the Internet, with nearly 550 million visits in September. KrebsOnSecurity received a letter last week from a reader whose friend received a targeted phishing message on the Booking mobile app just minutes after booking a hotel in California.
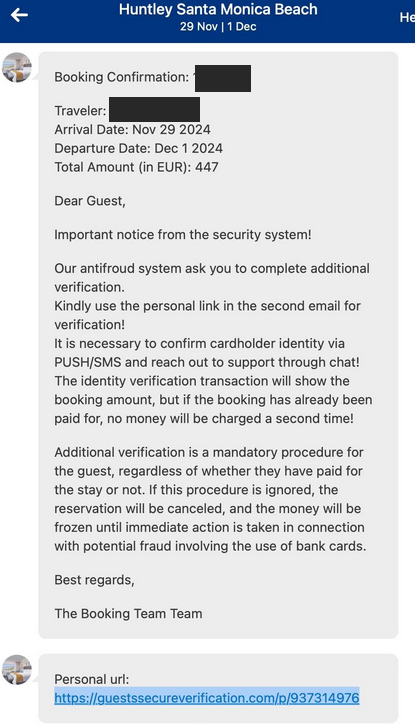
The letter included the hotel name and cited details from the reservation, claiming that Booking.com’s anti-fraud system needed more information about the customer to finalize the reservation.

Phishing email received by our reader’s friend after booking on booking.com in late October.
Booking.com confirmed in an email to KrebsOnSecurity that one of its partners experienced a security incident that resulted in unauthorized access to customer booking information.
Booking.com responded: “Our security team is currently investigating the incident you mentioned and can confirm that this is indeed a phishing attack targeting one of our accommodation partners. Unfortunately, this is not a new situation. And it’s common across industries. “Importantly, we want to clarify that Booking.com’s internal systems were not compromised. “
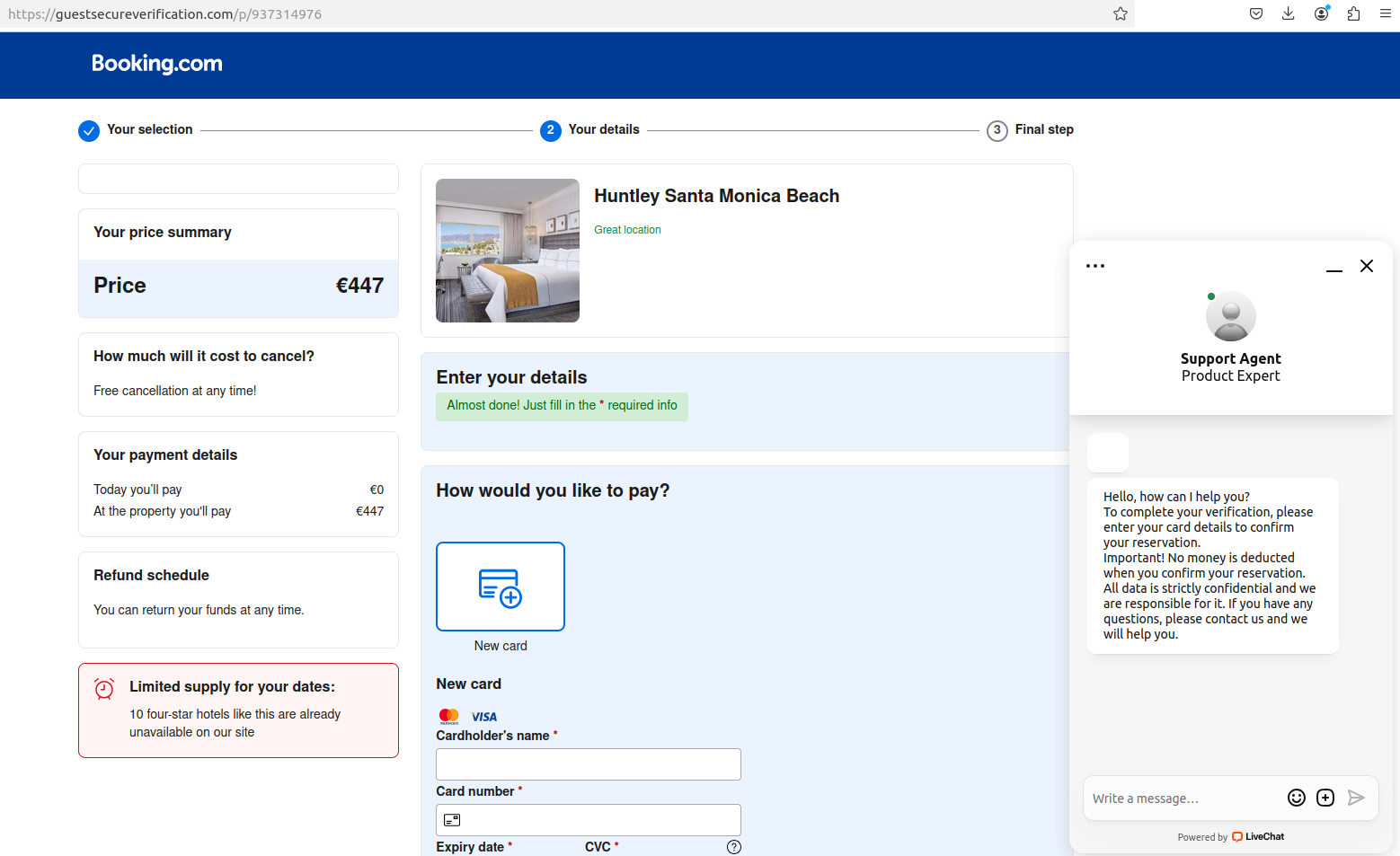
A fake booking.com website generated by visiting a link in a text message.
Booking.com says this now 2FA requiredwhich forces partners to provide a one-time password from the mobile authentication app (Pulse) in addition to their username and password.
“2FA is required and enforced, including allowing partners to securely access customers’ payment details,” a Booking.com spokesperson wrote. “That’s why cybercriminals follow up with messages to try to get customers to use our Make payments outside the platform.”
“That is, the phishing attack resulted from a partner’s computer being compromised with malware, which allowed them to access the partner’s account and send reader-marked messages,” they continued.
However, it’s unclear whether the company’s 2FA requirements apply to all partners or only newer ones. Booking.com did not respond to questions about the situation. Account Security Advice Customers are urged to enable 2FA.
A scan of social media networks shows this is not an uncommon scam.
In November 2023, security company Safety engineering Detailed How scammers target booking.com hotel partners with data-stealing malware. SecureWorks said the attacks have been occurring since at least March 2023.
“The hotel did not enable multi-factor authentication (MFA) on its Booking.com access, making it very easy to log into the account using stolen credentials,” SecureWorks said of the Booking.com partner it investigated.
June 2024, booking.com tell the bbc Phishing attacks targeting travelers have increased by 900%, with thieves leveraging new artificial intelligence (AI) tools being a major driver of this trend.
Booking.com told BCC it has begun using artificial intelligence to combat AI-based phishing attacks. A statement from Booking.com said their investments in this area “prevented 85 million fraudulent bookings from more than 1.5 million phishing attempts in 2023.”
Domains from the fake booking.com website sent to our readers’ friends— Guest security verification[.]com — Registered to email address ilotirabec207@gmail.com. according to domaintools.comthis email address has been used to register more than 700 other phishing domains in the past month alone.
Many of the more than 700 domains appear to target hotel companies, including booking.com and Airbnb. Others appear to be designed to target phishing users Shopping, steamas well as various financial platforms. Provides a complete, modified list of domain names here.
A cursory review of recent posts on dozens of cybercrime forums monitored by security firms Intel 471 Shows significant demand for stolen Booking.com accounts belonging to hotels and other partners.
A post on a Russian-language hacker forum last month Bhav Up to $5,000 available per restaurant account. The seller claimed to be helping people monetize hacked booking.com partners, apparently by using stolen credentials to set up fraudulent listings.
A service advertised on the English speaking criminal community Violation Forum In October, we provided assistance to phishers who may need assistance with certain aspects of phishing campaigns targeting booking.com partners. These include more than two million hotel email addresses, as well as a service designed to help phishers organize large volumes of phishing records. Customers can interact with the service through automated Telegram bots.
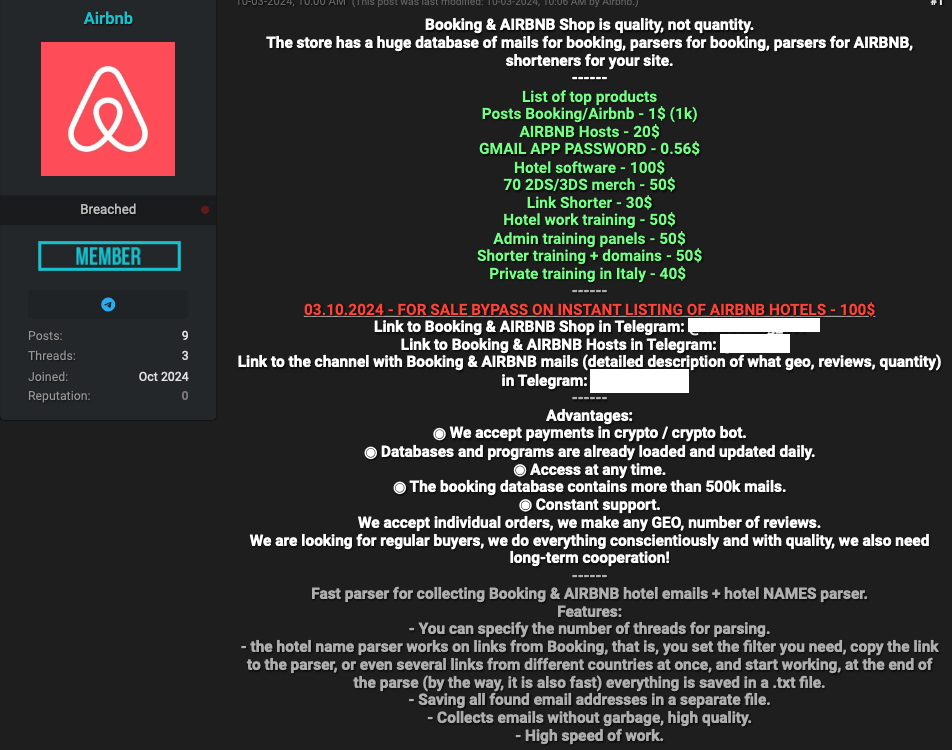
Some cybercriminals appear to be using compromised booking.com accounts to support their own travel agencies and other scammers, offering discounts of up to 50% on hotel bookings through booking.com. Others are selling ready-to-use “setup” files designed to simplify automated login attempts for booking.com administrator accounts.
SecureWorks discovered that phishers targeting booking.com partner hotels were using malware to steal credentials. But today’s thieves can easily access online criminal bazaars and purchase stolen credentials for cloud services that don’t enforce 2FA on all accounts.
that is what happened Working with numerous customers of the cloud data storage giant over the past year snowflake. In late 2023, cybercriminals discovered that while a large number of companies were storing large amounts of customer data in Snowflake, many of those customer accounts were not protected by 2FA.
Snowflake responded by requiring all new customers to enforce 2FA. But the change comes after thieves used stolen credentials to steal data from 160 companies, including AT&T, loan tree and Ticket Master.
2024-11-01 21:12:38