How to know if a USB cable is hiding malicious hacker hardware

We expect USB-C cables to perform a specific task: transfer data or files between devices. We didn’t think much about it, but rogue USB-C cables do a lot more than we expected.
These cables hide malicious hardware that can intercept data, eavesdrop on calls and messages, or in the worst-case scenario, take complete control of your computer or phone. The first one appeared in 2008, but at the time they were very rare and expensive, which meant the average user was largely protected.
Since then, their availability has increased 100-fold, and they are now sold as “spy cables” by professional spy retailers, as well as by unscrupulous sellers passing them off as legitimate products, making them easy to accidentally buy and be hacked. So, how do you know if your USB-C cable is malicious?
Further reading: We tested 43 old USB-C to USB-A cables. 1 Awesome. 10 is dangerous
Identifying rogue USB-C cables
Identifying rogue USB-C cables is not easy because they are designed to look like ordinary cables. Scanning technology is largely considered the best way to eliminate the essentials, which is what industrial scanning company Lumafield (known for its Lumafield Neptune industrial scanner) recently demonstrated.
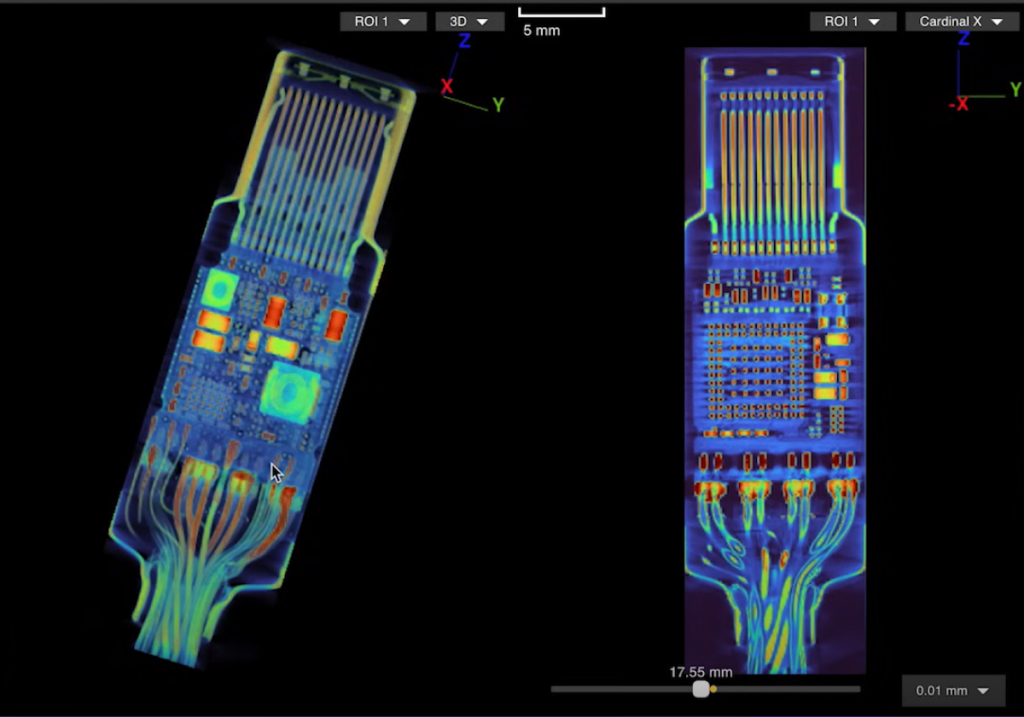
The company used 2D and 3D scanning technology on the O.MG USB-C cable, a well-known hacker cable designed for covert field use and research. It hides an embedded Wi-Fi server and keylogger in the USB connector. PCWorld Executive Editor Gordon Ung 2021 has it coveredsounds terrible.
Luma Field’s findings are interesting to say the least. A 2D X-ray image could identify the cable’s antenna and microcontroller, but only a 3D CT scan could reveal another wire connected to a die stacked on top of the cable’s microcontroller. You can explore a Scanned 3D model Please visit the Lumafield website.
Malicious hardware can be seen through 3D CT scans.
Luma Field
It confirms the worst-case scenario – you can only definitively confirm that a USB-C cable harbors malicious hardware through a 3D CT scanner, which you can’t do unless you’re a medical radiographer or a 3D industrial scientist. So, here are some tips to avoid and identify suspect USB-C cables without high-tech equipment:
- Buy from reputable sellers: If you don’t know and trust the brand, don’t buy it. Manufacturers such as Anker, Apple, Belkin and Ugreen have strict quality control processes to prevent malicious hardware parts from entering the cables. Of course, the other reason is simply that you’re getting a better product – 3D scanning similarly reveals how less reputable brands lack proper USB-C components, resulting in substandard performance. If you’re in the market for a new cable now, see our The first choice for USB-C cables.
- Look for warning signs: Look for brand names or logos that don’t look right. Weird markings, wires with inconsistent lengths or widths, and USB-C connectors that emit heat when not plugged in can all be signs that the USB-C cable is malicious.
- Using O.MG Rogue Cable Detector: this O.MG detector Claims to detect all malicious USB cables.
- Use data interceptors: If you’re just charging without transferring data, the interceptor will make sure no data is extracted. In addition to detecting rogue USB-C cables, the O.MG Rogue Cable Detector also acts as a data interceptor.
- To use detection services: If you’re handling extremely sensitive data for a business or government organization, you may want to use the services of a company like Lumafield to detect rogue cables with 100% accuracy. There is a fee for any such service, but it may be a small price to pay for safety and peace of mind.
If this article opened your eyes to the cunning tactics hackers use to steal your data, you’re not alone. Rogue USB-C cables are still not widely known. That being the case, be sure to share the above tips with your family and friends. The more people take the time to protect their data, the safer we will be in the long run.
Further reading: Buying a USB-C cable? 6 pitfalls to watch out for
2024-12-22 15:11:50