Tag: Hacker

December 22, 2024
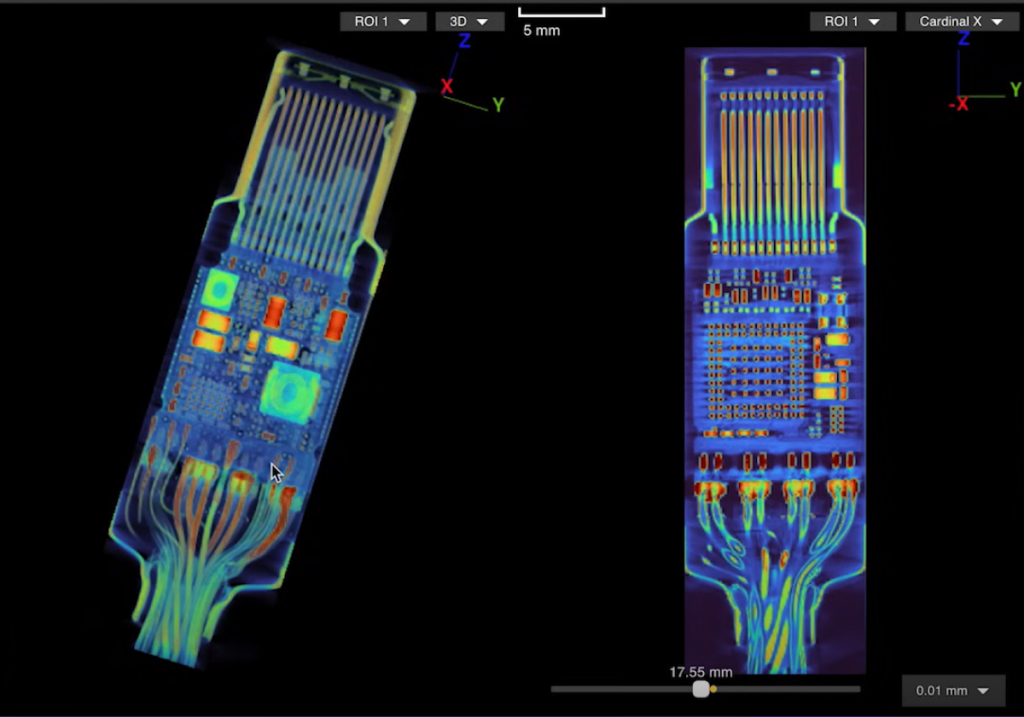
How to know if a USB cable is hiding malicious hacker hardware
December 11, 2024
U.S. Offered $10M for Hacker Just Arrested by Russia – Krebs on Security
December 10, 2024
Hacker in Snowflake Extortions May Be a U.S. Soldier – Krebs on Security
December 10, 2024
